The Basics of WhatsApp Forensics: A Beginner’s Guide
 Devarshiba Zala
Devarshiba Zala


The Basics of WhatsApp Forensics: A Beginner’s Guide
WhatsApp is, certainly, the most popular instant messaging application. It provides free cross-platform messaging and VoIP (Voice over Internet Protocol) services to its users.
WhatsApp was first released for public use in 2009 on the App Store for iPhones. It was supposed to serve as an alternative for the standard short message service (SMS) on mobile devices.
With over 2 billion users in over 180 countries, WhatsApp is easily the most popular and widely-used messaging application across devices. And with over 100 billion messages sent every day on the platform, WhatsApp is definitely one of the most frequently used apps in general.
Since its release, over the years, WhatsApp has grown to introduce applications for all mobile operating systems (Android, BlackBerry OS, Windows Phone, and others). WhatsApp developers also released the WhatsApp web client (which can be used on all major web browsers on PCs and Macs) and the
WhatsApp desktop application (for Windows OS and macOS).
These growing technologies led to cybercrimes and cyber frauds; which led to forensic investigation of the data and to write this forensic article.
FEATURES:
WhatsApp has introduced many advanced features in comparison to the other instant messaging application. Some of the features are as follows:
- Chat Lock
- Disappearing Messages
- Silence unknown caller
- Encrypted Backups
- Media Sharing; Media like photos, videos, ZIP files, documents, etc.
- WhatsApp also has a feature where you can share the media with or without METADATA.
- WhatsApp Pay
- WhatsApp Web
- WhatsApp Business
- Archive Chats
Backup folders within the Android Device:
Android WhatsApp creates daily backups of chat databases within the device, encrypting them with a key stored in the Application Sandbox. WhatsApp backup files are accessible through the Media Transfer
Protocol (MTP) when connecting a device to a computer via USB.
Chat databases in the backup folder are encrypted in the CRYPT14 or CRYPT15 format, while media files are stored as-is. Earlier it used to encrypt in the CRYPT12 format.
Backup folders within the iOS Device:
WhatsApp is a messenger that does not keep users’ communication history on its servers. Instead, it employs user devices to store and back up its data. When analysing an iOS device, you can find
WhatsApp data in the following locations:
- Device internal storage: The primary location where WhatsApp keeps its data is the device’s built-in memory. The WhatsApp database files on iOS devices are stored within the app’s
sandboxed directory, making them difficult to access unless the device is jailbroken.
You can find the database file in the following path:
“/private/var/mobile/Containers/Shared/AppGroup/<AppGroupID>/ChatStorage.sqlite “
- iCloud backup: WhatsApp enables users to set up automatic backups to iCloud. Though users can schedule backups daily, weekly, or monthly, they can also turn them off.

iTunes backup: Additionally, WhatsApp data is saved when users create iTunes backups of their iOS devices. When it comes to iOS devices, all WhatsApp data can be extracted in a basic iTunes backup procedure. However, for Android devices, we often recommend a physical extraction method to recover WhatsApp’s evidentiary files.
Google Account cloud storage:
Users can opt to upload WhatsApp backups to their Google Account cloud storage. Like on devices, media files in these backups are stored as-is, and databases are by default encrypted in the CRYPT14 format.
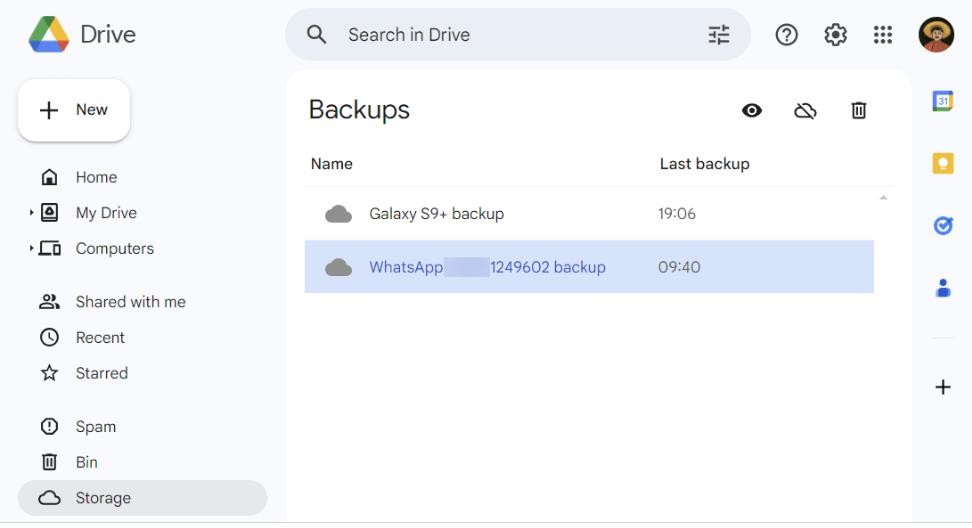
Fig.2: Backup in Cloud
Google Drive does not provide a way to download the files directly, so you will need a specialized tool to obtain them.
WhatsApp Modified Versions :
A WhatsApp mod apk is a modified version of the WhatsApp application. They are designed by third- party developers or individuals who want to incorporate additional functionality to the official WhatsApp version. There are allot of modified versions for Android OS devices. Some of the versions are as follows :
- GBWhatsApp
- FMWhatsApp
- OBWhatsApp
- WhatsApp Plus
- YoWhatsApp
End-to-End Encryption :
The WhatsApp end-to-end backup encryption option offers additional protection for backups. It involves securing access to backup files with a password or 64-digit encryption key and encrypting the database file in CRYPT15 format. If a user activates this protection, the application chats can only be restored from a backup with the additional password or key. Note that this setting affects both the files uploaded to the
cloud and those stored on the device.
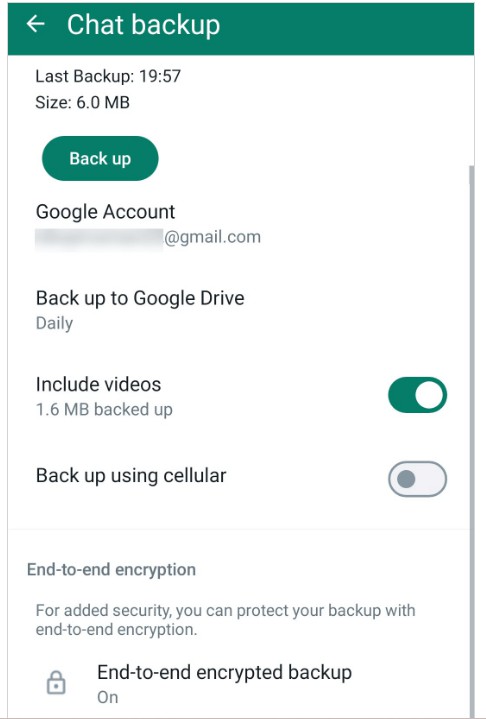
Fig.3: Backup Encryption options in Android WhatsApp settings
WhatsApp’s popularity on smartphones—in terms of users—did not completely translate to computers, but millions of people still use WhatsApp on their PCs and Macs. Invariably, on computers, WhatsApp web client (for browsers) and the WhatsApp desktop application are the objects of interest for us in this guide.
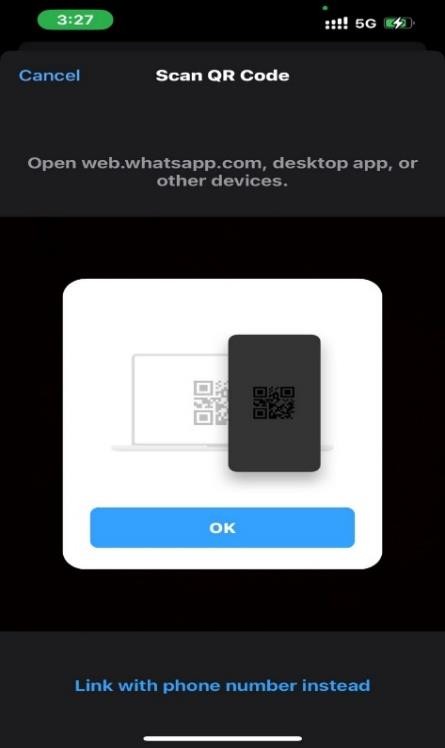
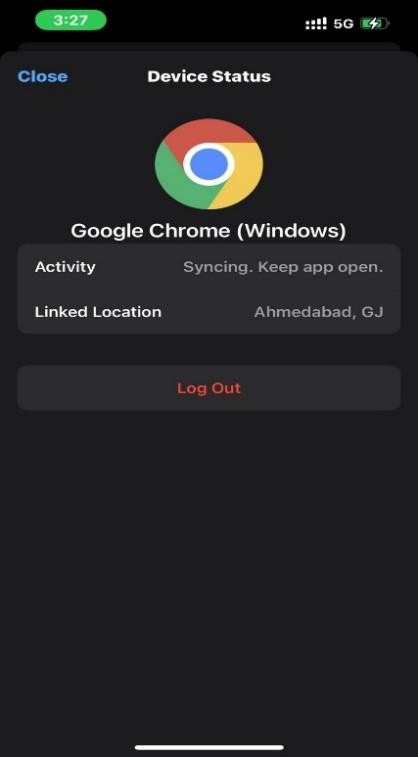
Fig.4: Linked Devices
WhatsApp Web :
A user simply has to visit the WhatsApp web page on a supported browser and then scan the QR code there using the WhatsApp app on their smartphone (usually an iPhone or Android device).
These are the supported browsers: Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari.
On Windows 10, Chrome stores its files in the folder along this path :
C:\Users\ ABC \AppData\Local\Google\Chrome\User Data\Default
You will find the WhatsApp web client (when used on Chrome) files here :
Users\ABC\AppData\Local\Google\Chrome\User Data\Default\IndexedDB\https_web.whatsapp.com_0.indexeddb.leveldb\ {######}.log
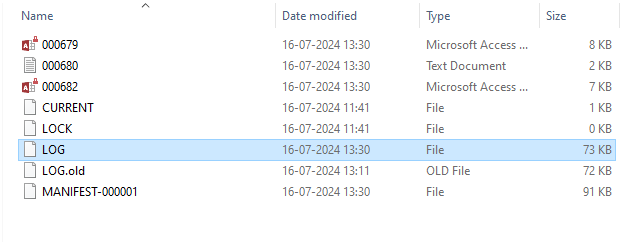
Fig.5: Log File for WhatsApp Web
WhatsApp Desktop Application :
The user must navigate to the WhatsApp download page, download the appropriate package, and execute the file to install the application. Post-installation, the user will need to scan a QR code, similar to the one used for the web client, to complete the setup.
The WhatsApp desktop application files are likely to be found at the following directory path. :
C:\Users\ABC\AppData\Local\Packages\5319275A.WhatsAppDesktop_cv1g1gvanyjgm\LocalState
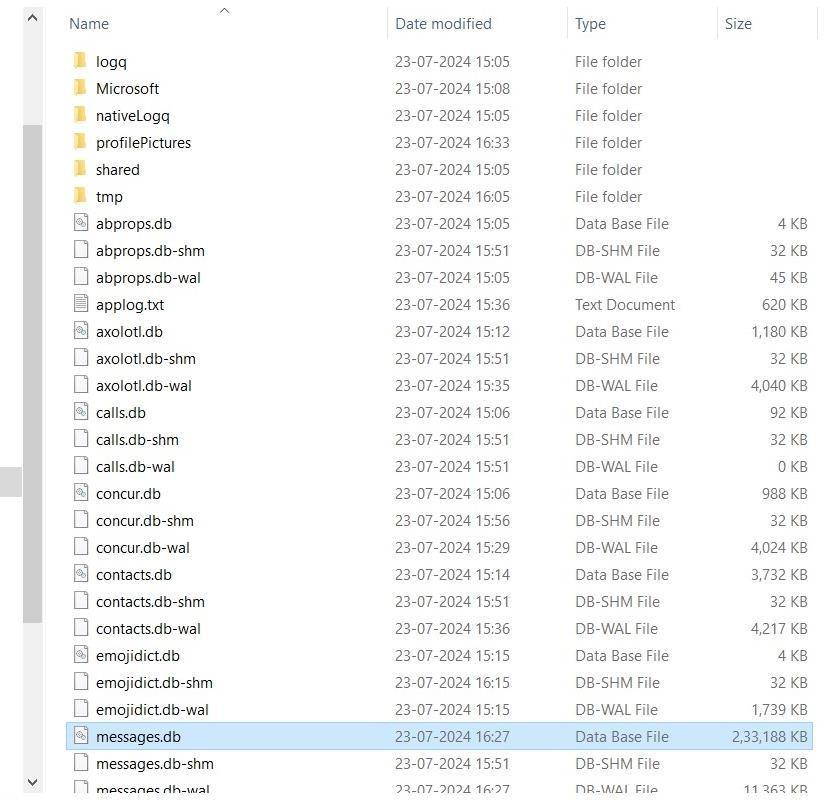
Fig.6: Database for WhatsApp Desktop Application
Additionally, you may want to verify these paths as well :
- \Program Files (x86) \WhatsApp\
- \Users\ABC\AppData\Local\WhatsApp\
- \Users\ ABC \AppData\Local\VirtualStore\Program Files (x86) \WhatsApp\
Forensic Methods :
There are different methods for WhatsApp Forensics. Some of them are as follows :
- Data Extraction Tools: There are various forensic tools available that can extract data from smartphones, including WhatsApp data. Tools like Cellebrite UFED, Oxygen Forensic Detective, and Magnet AXIOM are commonly used for this purpose. These tools facilitate the forensic collection, extraction, and analysis of WhatsApp data. These tools are compatible with all types of smartphones.
- Emulators: Android emulators are virtual machines that function similarly to physical mobile devices. These emulators can be customized according to specific requirements for the collection and extraction of WhatsApp data.
Conclusion :
In conclusion, WhatsApp forensics is an increasingly vital aspect of digital investigations, given the platform’s widespread use and the wealth of information it can contain. By utilizing specialized tools and techniques, investigators can effectively collect, extract, and analyse WhatsApp data from various devices, including leveraging Android emulators for enhanced flexibility. As technology evolves, staying updated with the latest forensic methods is essential for ensuring thorough and accurate investigations. Ultimately, mastering WhatsApp forensics is crucial for uncovering critical evidence and supporting legal processes in today’s digital age.
Unveiling the Secrets of Digital Security: How to Safeguard Your Online Presence
Top authors
Related Blogs
Cyber Security
The Human Hack: Understanding Social Engineering Attacks
 Rushit Soni |
Rushit Soni |


You’ve probably heard the story – an email from a Nigerian Prince, promising a fortune if you could just send...
Cyber Security
The FBI’s Latest Warning on Silent Ransom Group:What Law Firms Need to Prepare For
 Rushit Soni |
Rushit Soni |


Earlier this month, the FBI released a Private Industry Notification (PIN), warning about the Silent Ransom Group (SRG), also known...
Cyber Security
Unveiling the Secrets of Digital Security: How to Safeguard Your Online Presence
 Rushit Soni |
Rushit Soni |


In an increasingly digital world, securing your online presence has become more important than ever. From personal information to financial...



